catalogs
4. Authentication authorization
1. Networking
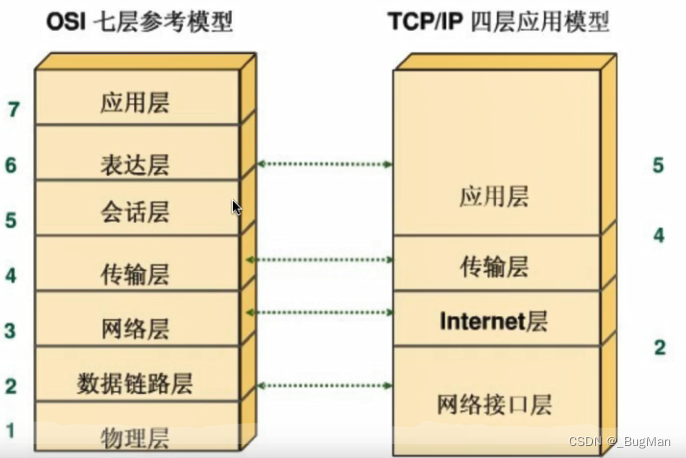
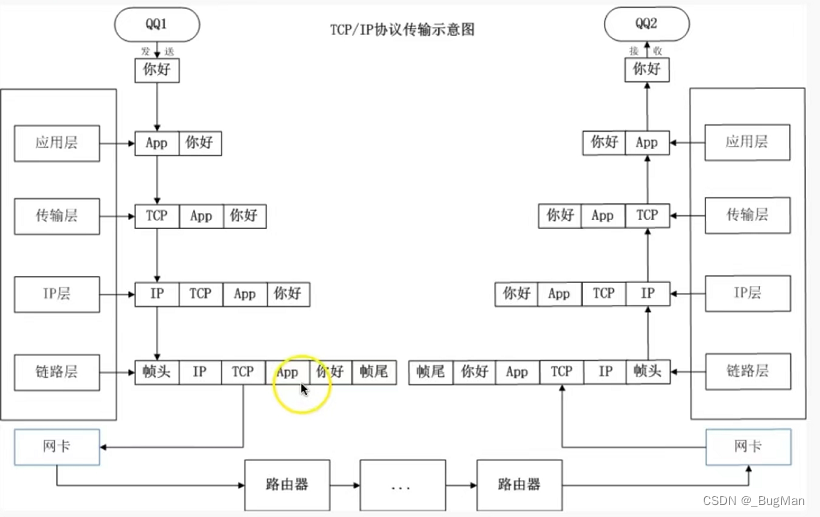
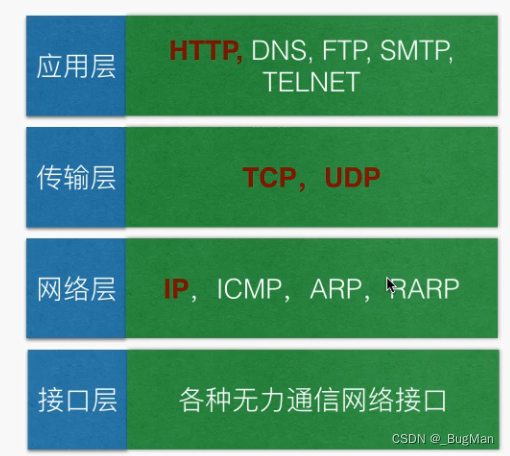
Computer networks: Computer network, a set of topologies consisting of nodes and edges. The edge, or link, is the backbone link between routers, and the link between routers and hosts is the access link. A node, i.e., a host node or a data exchange node, consists of either a host or a data exchange device (or a higher-level load balancing device) Layering: According to the different functions responsible for the computer network in the logical layering? The classic model is the OSI seven layers, but seven layers is slightly cumbersome, generally with TCP / IP four layers can briefly explain the role of layers in the network layering. TCP/IP four-layer hierarchy:- application layer (computing) application
- transport layer Providing end-to-end communication, the transport layer provides transparent data transfer between end users and reliable data transfer services to the upper layers. The transport layer ensures the reliability of data transmission through flow control, segmentation/reorganization and error control on a given link.
- network layer The IP layer, which is responsible for handling the transmission of IP data messages in the network, the IP layer transmits IP data messages, with the help of a routing table, from one end of the network to the other, in short, IP implements the routing of packets, IP protocols and routers work at the network layer.
- network interface layer This includes the operating system’s device driver and the network card, which together handle the details of the physical interface with the transmission medium (fiber optics, etc.).
2.HTTP
HTTP, Hypertext Transfer Protocol, was chosen as the application layer protocol for the WEB system.2.1. Message structure
2.1.1. request message
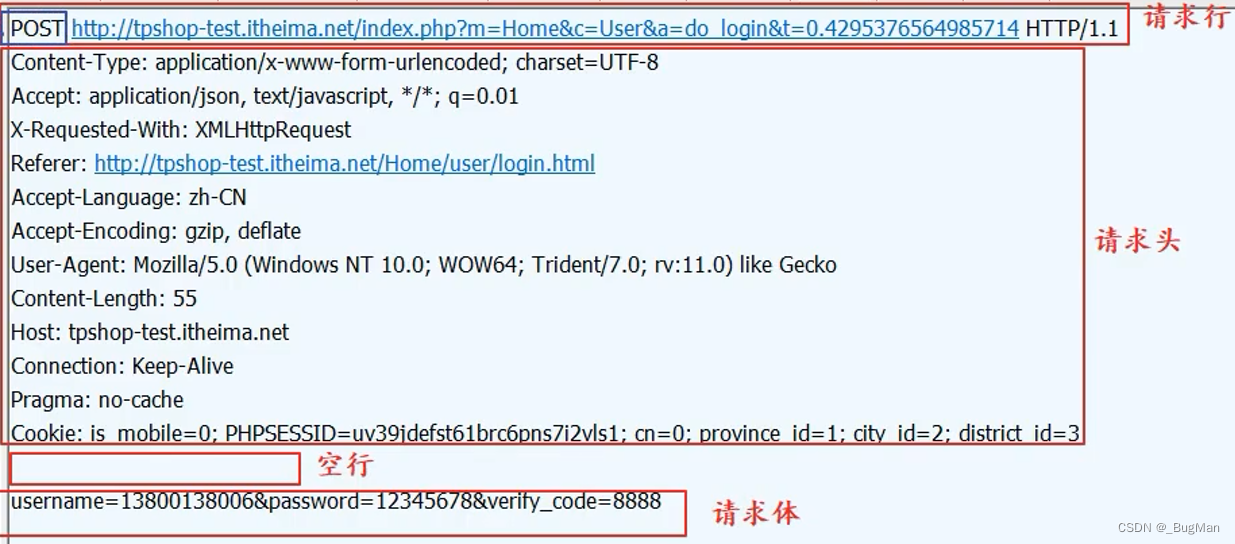
HTTP request message (request) consists of four parts: request line (request line), request header (header), blank lines and request data (request data)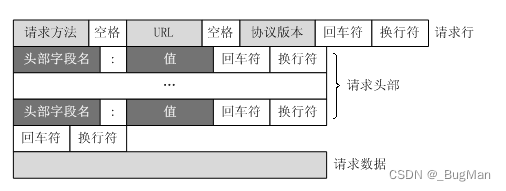
| name | corresponds English -ity, -ism, -ization |
|---|---|
| requesting line | Record request method, URL, HTTP protocol version number |
| request header | Record some additional information as key-value pairs, such as cookies, encoding, host, etc. |
| Request data | The request data, also called the request body, is not used in the GET method, but in the POST method, which is used in situations that require the client to fill out a form. There are two important keys related to the request data in the request header: Content-Type and Content-Length. |
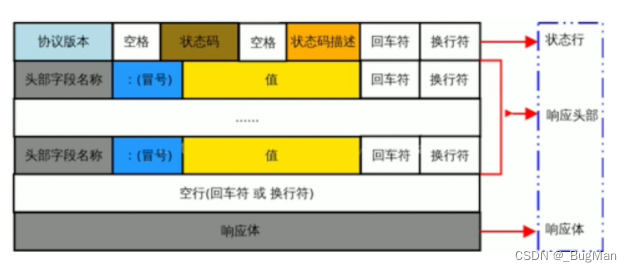
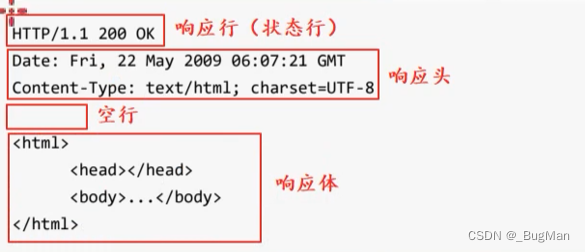
2.1.2. Response message
The two most important parts of the HTTP response message (response):- status code Record the status of the response
- response body Record the response data, which can be is a web page (HTML code), is an image, video, audio, etc.
2.2. Methodology
HTTP has a total of GET, POST, PUT, DELETE, CONNECT, HEAD, originally designed with the intention of each operation on the server have a corresponding method, but in actual use found that in fact, GET, POST two methods are enough, GET is responsible for the server to ask for data, POST is responsible for the server to store data. GET, POST difference:| name | specificities |
|---|---|
| GET | Parameters in the URL, data size can not exceed 2KB |
| POST | The data is in the “request data” area of the HTTP message, and theoretically there is no upper limit to its size. |
2.3.HTTPS
https=http+ssl/TSL, i.e. use HTTP for communication and SSL/TLS for data protection. In the https system, SSL/TLS is an intermediate layer between the HTTP protocol (application layer) and TCP (transport layer).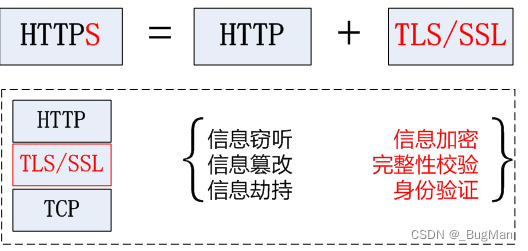
- Content encryption: hybrid encryption technology is used so that intermediaries cannot directly view plaintext content
- Verify identity: authenticate that the client is accessing its own server through the certificate
- Protecting data integrity: preventing transmitted content from being impersonated or tampered with by intermediaries
2.4. Cross-domain
The cross-domain problem stems from the “same-origin policy”, which is a convention that essentially restricts JavaScript scripts in one domain from interacting with content in another domain. The “same-origin policy” is a core mechanism to ensure the security of the browser, all browsers must implement this mechanism in the implementation, otherwise the browser will be very easy to be attacked. The so-called “same-origin”, that is, in a domain, a domain consists of three parts: protocol, host, port, any one of which is different, is not a domain, a source. for examplehttp://www.test.comHer js in this page cannot interact with content in other domains. This handoff prohibits interaction not in the sense that cross-domain requests can’t be sent, but in the sense that the results of the response are intercepted by the browser. Therefore, it is very convenient to solve the cross-domain problem in the back-end, as long as in the response to return to deal with the browser to determine whether the response is cross-domain conditions on the line.3. Session Hold
3.1. Overview
Session keeping technology came into being because HTTP is a stateless protocol, this request has nothing to do with the previous request, they can’t perceive each other, what did the previous request do? What the last request did? This request is completely unaware of the session maintenance technology is to a third-party design to realize the connection between HTTP requests, so that the requests can be mutually aware of each other. The two current conferences will maintain the technology:- cookie
- session
- Way 1. The school prepares a roster and compares them one by one as they come in the door.
- Mode 2. Students get a student card and enter and exit with it.
3.2.cookie
Client-side technology, where the state (data) is saved on the client side, i.e. the student card accesses the campus this way. The server returns an unlimited number of cookies to the client, one cookie being a key-value pair. The carriers of cookies during client-server interaction are request and response.public class DemoServlet extends HttpServlet {
@Override
protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
Cookie[] cookies=request.getCookies();
if(cookies!=null){
for(Cookie cookie:cookies) {
if("LastLoginTime".equals(cookie.getName())) {
System.out.println("Time of last visit: " + cookie.getValue());
}
}
}else{
System.out.println("This is the first login!") ;
}
Cookie cookie=new Cookie("LastLoginTime",System.currentTimeMillis()+"");
cookie.setMaxAge(60*60*24);//set the expiration date to one day
response.addCookie(cookie);
}
}3.3.session
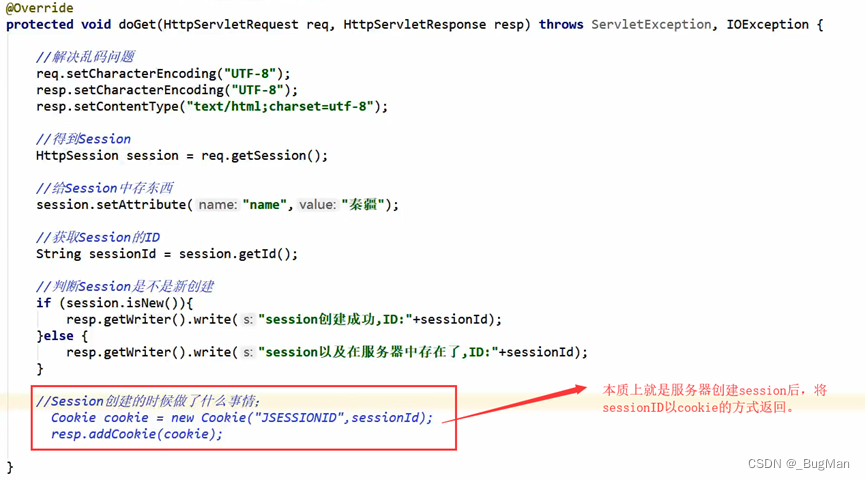
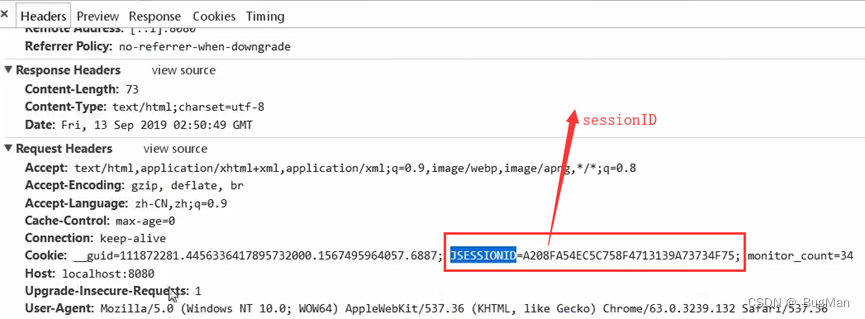
Server technology, i.e., the state (data) is saved on the server side, i.e., the roster enters the campus this way. Like cookies, the carrier of session during client-server interaction is also request, response. session generation: A session is not automatically created when a client accesses the server, but must be generated by specifying the API:session destruction:request.getSession()
- session.invalidate()
- Two requests before and after exceeded the life cycle time specified by the session.
4. Authentication authorization
4.1.Token
A token, also known as a “token”, is a credential that verifies a user’s identity. the composition of the token is arbitrary, and can identify the user’s identity. token’s workflow: The client sends a request to the server, the server receives it and generates a token to be returned to the client, and thereafter any authentication of the client is based on this token.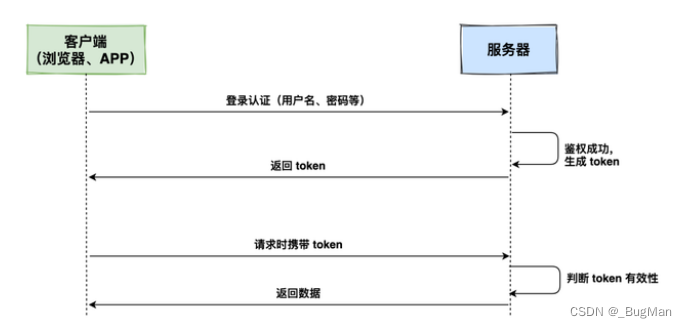
4.2.JWT
JWT, Json web token, that is, a json based universal token standard , token is inherently arbitrary , JWT specifies the format of the token . JWT specifies that the token consists of three parts: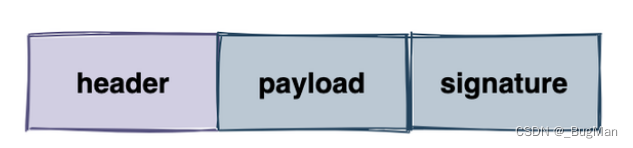
- header
The header, which carries two pieces of information:
- Declare the type, i.e. declare that this is jwt
- Declare the encryption algorithm, HMAC SHA256 encryption algorithm is used by default.
- payload Load, where valid information (data information) is stored.
- signature
The visa, which can be used to verify the integrity of the entire token and whether it has been tampered with, consists of three parts:
- header (after base64)
- payload (after base64)
- secret Private key
