
Cybersecurity is a large and growing field that encompasses several areas of specialization, such as network defense, cyberattacks, data encryption, and more. Introduces the basic concepts, techniques, and tools of cybersecurity, going step-by-step to help you become a competent cybersecurity practitioner.
I. Network security basics
1. Basic computer knowledge
Understanding the basics of computer hardware, software, operating systems, and network architecture can help you better understand the concepts and techniques of network security.
2. Network basics
Understanding the structure, protocols, services, and security of networks can help you better address the principles and techniques of network security.
3. Security basics
Understanding the concepts, principles, intimidation and attack methods of security can help you better understand the significance and necessity of cybersecurity.
II. Network security technologies
1. Network security protection technology
Network security defense technologies are those that protect networks from attacks and intrusions, including defense firewalls, intrusion detection and prevention systems, anti-virus software patches, and vulnerabilities.
2. Network security attack techniques
Network security attack techniques are those that use vulnerabilities, exploits, and flaws to attack and intrude into networks, including Trojans, worms, menorrhagia, and DoS.
3. Network security penetration testing technology
Network security penetration testing techniques are techniques that simulate the behavior of an attacker to test the robustness and effectiveness of network security protection measures, including information collection, deletion, leakage of use, elevation of privileges, data leakage, and so on.
III. Network security tools
1. Network security protection tools
Network security protection tools are software and hardware devices used to protect network security, including firewalls, IDS/IPS, anti-virus software, VPNs, and so on.
2. Network security attack tools
Cybersecurity attack tools are software and hardware devices used to conduct cyber attacks and access, including Nmap, Metasploit, Aircrack-ng, and others.
3. Network security penetration tools
Network Security Penetration Tools are software and hardware devices used to measure the guidelines for network security protection measurements, including Nessus, Burp Suite, Kali Linux, and more.
IV. Cybersecurity implementation
1. Network security strategy development
A network security policy is a set of rules, implementations, and procedures developed to protect the security of a network, including password policies, network access control, and emergency response response plans.
2. Cybersecurity incident response
Cybersecurity incident response refers to the discovery of a cybersecurity incident and a series of actions to protect cybersecurity, including incident analysis, data remediation, and security.
3. Cybersecurity training and awareness
Cybersecurity training and awareness is an activity that directs employees and users to provide training in cybersecurity knowledge and skills, as well as to publicize cybersecurity policies and implementations.
V. Future trends in network security
1. Artificial Intelligence and Machine Learning in Cybersecurity
Artificial intelligence and machine learning can help cybersecurity practitioners better detect and respond to cyberattacks and improve the efficiency and accuracy of cybersecurity protection.
2. Development and application of cloud security
With the popularization and application of cloud computing technology, cloud security will become one of the important territories of network security, which requires continuous development and innovation.
3. Application of blockchain technology in network security
Blockchain technology can provide more secure and reliable network security solutions such as digital authentication, password management, and network access control.
This is a brief overview of the basics, techniques, tools, practices and future trends in cyber security. To become a bona fide cybersecurity practitioner and, one needs to raspingly bake and pay attention to the latest developments and trends in the field of cybersecurity.
VI. Common network security problems and solutions
1. Virus and malware protection
Viruses and malware are one of the most common threats in cyber security. To prevent virus and malware attacks, antivirus software should be updated regularly and operations should not maintain the system, strangers’ emails and files, not download unknown software, etc.
2. Network password security issues
Passwords are one of the most important aspects of network security. To ensure password security, you should choose strong passwords, change passwords regularly, don’t use the same passwords and don’t use login names to use programs.
3. Social engineering attacks
Social engineering attacks are attacks in which the attacker utilizes the weak points of a person, such as obtaining passwords and sensitive information through deception and fraud. In order to prevent insurgency it is important to be more security conscious and less likely to trust information and requests from strangers.
4. Phishing attacks
Phishing attacks are when attackers disguise themselves as reliable entities, such as banks, e-commerce companies, etc., and fraudulently obtain sensitive information from users. To guard against cyber wrestling, confirm the authenticity and security of websites and do not easily click on suspicious links and attachments.
VII. Recommendations for network security resources
1. Domestic and foreign security organizations
These include the China Cyber Security Association in China and the International Security Alliance, one of the world’s largest security organizations.
2. Security information sites
Including domestic security guest, freebuf and so on, as well as international Dark Reading, Threatpost and so on.
3. Security Vulnerability Information Platform
This includes domestic Crow Cloud Vulnerability and Patchday Vulnerability, as well as international CVEs and NVDs.
4. Security tools and software
Includes Nessus, Burp Suite, Kali Linux, and more.
This is a brief overview of frequently encountered problems and solutions for cybersecurity and recommended cybersecurity resources. All practitioners, need to continuously learn and master the latest technologies and tools, and constantly improve security awareness and protection capabilities.
VIII. Development of the cybersecurity industry
Cybersecurity is a popular career field that is becoming more and more important as information technology continues to increase. Penetration engineers, security operations and maintenance engineers, and so on. For those who want to enter the field of network security, it requires a solid foundation in computer fundamentals and security knowledge, as well as the need to continually learn and keep up with the latest technologies and tools.
Cybersecurity leadership field job waiting is relatively high, depending on the different positions and geographical areas, the average annual salary of cybersecurity practitioners between 200,000 to 500,000 yuan. In addition to the network job waiting, all there are wide apart development prospects, the future demand in the field of network security will continue to grow, for the network security talents with certain experience and technology, career development space is very large.
IX. Summary
Network security is a very important territory, with the popularity of the Internet and the increasing degree of information technology, the importance of network security has become more and more prominent, in daily life and daily to protect personal information and privacy, improve security awareness, do not follow the consciousness of the leakage of sensitive information and passwords. For those who want to work from network security, you need to have a solid foundation in computer and error and security to master the latest technology and tools, and constantly improve the scope of protection and response capabilities.
X. Sharing of network security learning resources
1. Introduction to network security from a zero base
For students who have never been exposed to network security, I have prepared a detailed roadmap for your learning growth. Can be said to be the most scientific and systematic learning route, we follow this general direction of learning quasi no problem.
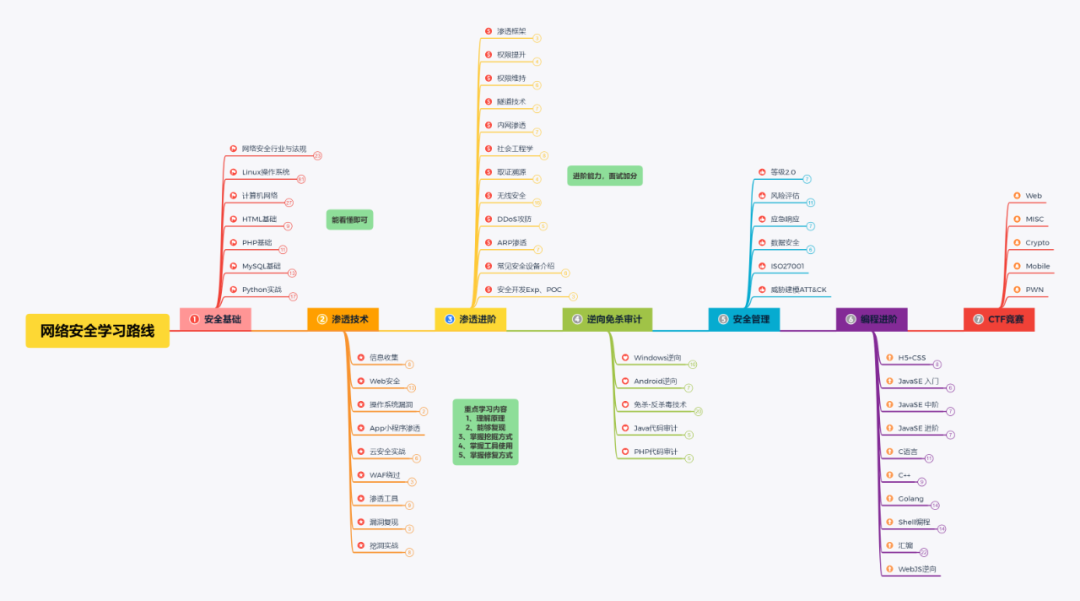
Also each growth path corresponds to a board with accompanying tutorial notes source code provided:
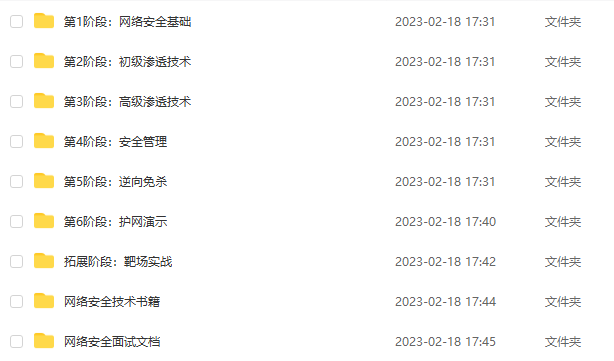
2. Network security video tutorials
Many of you don’t like obscure text, and I have prepared a video tutorial for you, which contains 21 chapters, each one a condensed version of the best of the current board.

3.SRC(computer) file& Hacking Books
Everyone’s favorite and most concerned SRC documents & hacking books are also included!

4. Information on Operation Protect the Net
Among them, the corresponding information has been prepared about HW’s net protection operations, which can be equivalent to the golden handshake of the competition!
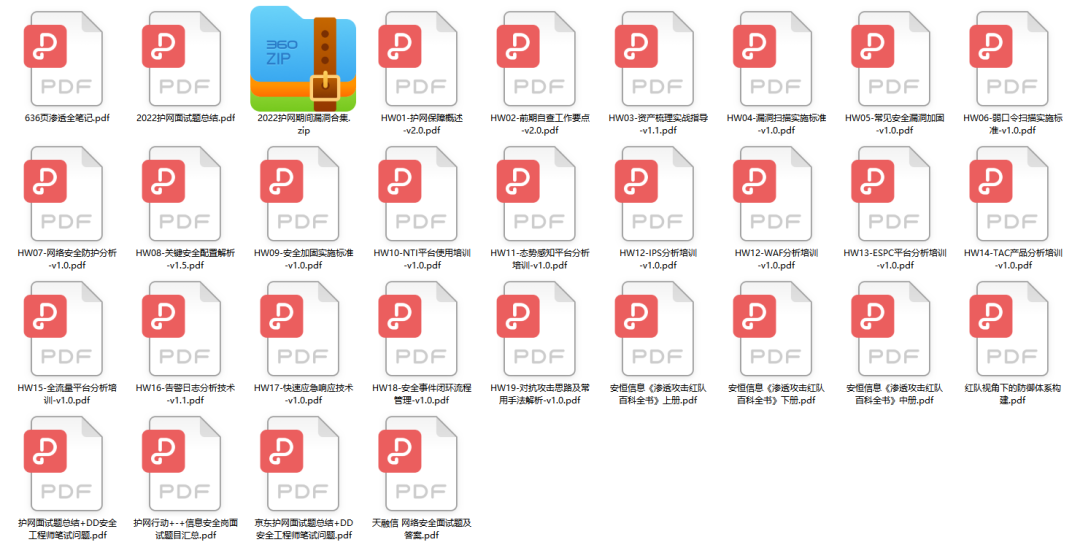
Tips
To get the full HD version of the above mind map and materials, you can reply to“Security”Automatic acquisition.
